The marketing profession’s awareness of online advertising fraud and non-human traffic (NHT) is steeply rising. A recent test attack by a group of experts on popular online video platforms including Google’s YouTube rated the platforms highly vulnerable to ad fraud.
“When the researchers sent the bots to visit two particular videos 150 times, YouTube’s public view counter identified only 25 of the views as real. However, AdWords, Google’s service for advertisers, charged the researchers for 91 of the bot visits.
In other words, Google’s core advertising engine charged the researchers for the bot visits even though YouTube was clearly able to identify them as fake.”
FT.com: Google charges for YouTube ads even when viewed by robots
Professionals (read the WPP POV here) and mainstream publications worldwide echoed the test results asking questions about how fraud is carried out. Here we give you three practical and eye-opening examples.
Video Ad Fraud on YouTube/Google AdX
In his post, fraud despiser Mike Nolet leads us through a simple but enormously effective scam involving YouTube. He sheds some more light on the subject brought up by the test attackers of the video platforms we mentioned above.
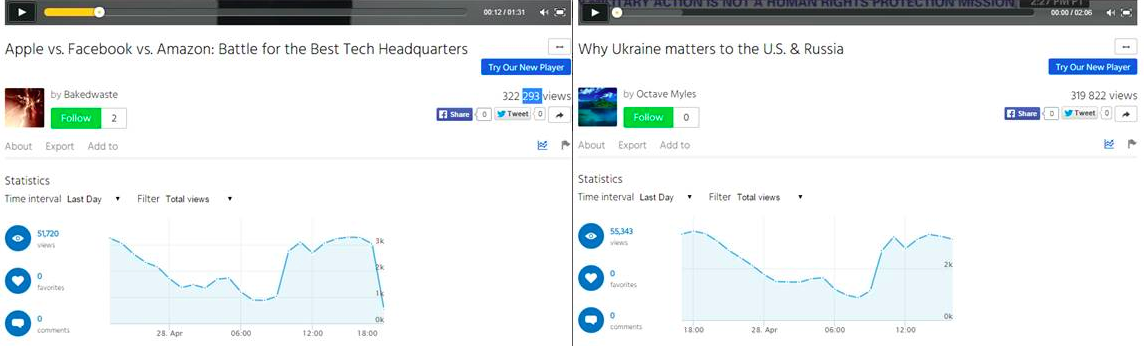
Mike was digging into the dirty laundry of Michaelgolf.com, a suspicious sports web site that apparently generated 161 million video impressions at an average CPM of $9.16 making it one of the top sites for the video inventory of Google AdX. 900 thousand unique users that on average saw 177 video ads per week. Hmm?
Michaelgolf.com appears to be legitimate with videos and banners. But the site hardly has anything to do with golf, there are no video ads on it, and it doesn’t take much to find out that the content is farmed and the banner ads are fakes. We checked it ourselves while writing the post. Some of the eyeballs on Michaelgolf.com could be human but a simple look on Alexa.com gives you an idea about the trick with the site’s traffic.
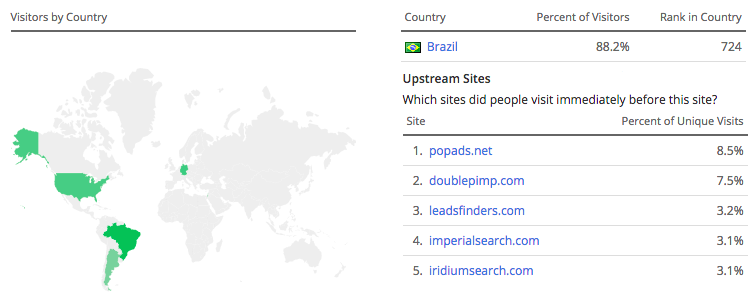
88% of Michaelgolf.com’s traffic is from Brazil (!) and the top referrers are trash networks, adware and porn sites. Most of the traffic is probably non-human but a bunch of bots. Dozens of other sites are also traced back to the same host. Not a terribly sophisticated scheme but could still be very lucrative for the criminals behind it.
You may ask where the video ads shown in the AdX inventory are if not found on the site? The majority of Michaelgolf.com’s traffic is from adware and the site performs various checks when viewed. It most probably doesn’t display any ads to chance visitors. For its botnet and trash traffic, however, it spams as many videos into a popup as it can. Hard to guess how much of the inventory can bypass ad verification but even one percent means $$$ for them.
Conficker is back
A worm is a computer malware that replicates itself in order to spread to other computers. Conficker is a worm that was first detected in 2008 and it is one of the largest known ones of its kind. Conficker is still with us and keeps infesting 7 years after.
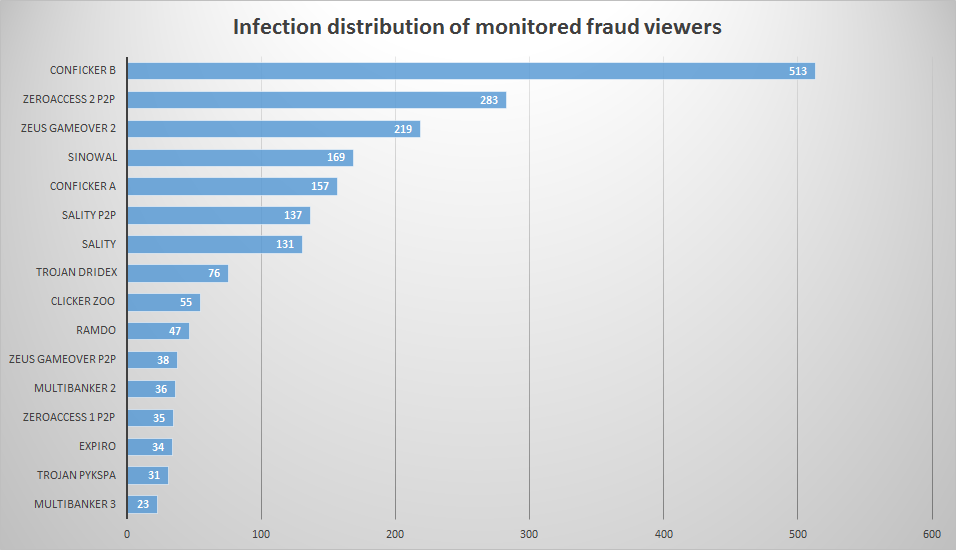
The anti-fraud detectives of the ad/traffic verification specialist enbrite.ly recently uncovered that in a campaign targeted at German internet users the variant Conficker B was behind 40% of the ad impressions delivered.
The campaign in question was running on a blind network meaning that advertisers don’t have access to any domain data, in simple terms: dirt cheap, potentially crap, no questions asked. Not that it should mean fraud though.
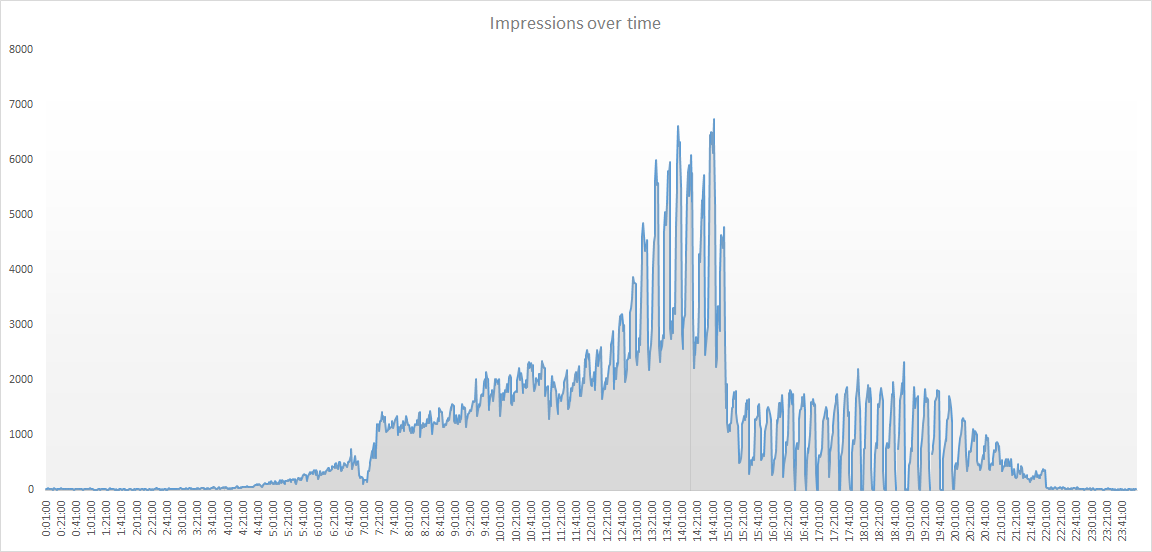
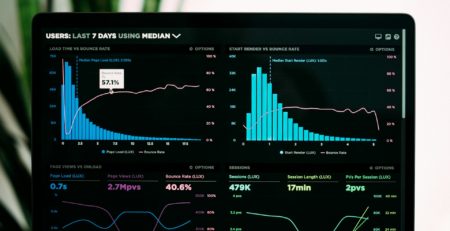
The botnet activated by the worm was first suspected from the highly unusual regular bursts of ad impression delivery shown as spikes in the diagram below. One ‘user’ generated as much as 200 ad impressions per minute. Virus tracking identified that the main botnet was infected with the malware Conficker B that was the apparent vehicle for ad fraud.
The infected browsers ‘visited’ fake front end sites with seemingly normal although very thin content where they triggered invisible browser windows in the background to run dozens of ads simultaneously.
Apart from Germany, Italy, the Czech Republic and Poland are the most affected markets by the Conficker infection on the Continent. enbrite.ly rightly advise online media buyers to protect their clients’ budgets by using the latest anti-fraud and ad verification technology.
Political bots
Sean Gourley, co-founder of the Quid augmented intelligence platform, explains in his exciting article in Wired Magazine’s “The world in 2015” special edition how artificial intelligence, learning algorithms and fake social networks are already used for political propaganda. A group of cybercriminals helping spread pro-Russia messaging by artificially inflating video views and ratings on a popular video website was uncovered by security specialists of Trustwave. The scheme was at first suspected to be a case of ad fraud but turned out to be something more than just that.
The method highlighted by Trustwave’s SpiderLabs blog could be used to increase the popularity of a piece of content, and in turn its visibility, whether it deals with advertising, or political issues. Fraudsters infect computers with trojan malware and force them to browse sites to generate ad revenue, as well as, fraudulent traffic.
The clips – non-political and political – involved in this traffic fraud scheme shared several characteristics including nearly identical number of views, zero shares/retweets/comments and similar distribution of views. The assumption drawn from the analysis is that botnet operators otherwise specialized in ad fraud repeatedly received orders to help spread political messages by artificially inflating the viewership in order to make the clips more visible to human target audiences.
It is and will be interesting to observe how the techniques of criminals and anti-fraud specialists evolve as the fraudsters are by now under a lot stricter scrutiny than ever before. The billions of dollars they pump out of the digital advertising ecosystem easily fuel the fraudsters’ cat-and-mouse game for years to come. Direct media buy from premium publishers or trusted networks is a relative safe haven but as Google’s example shows nobody is 100% safe. The bottom line: Find a partner to protect yourself against digital ad fraud.